DDoS protection quickstart guide shows how sFlow streaming telemetry and BGP RTBH/Flowspec are combined by the DDoS Protect application running on the sFlow-RT real-time analytics engine to automatically detect and block DDoS attacks.
This article discusses how to deploy the solution in a Cisco environment. Cisco has a long history of supporting BGP Flowspec on their routing platforms and has recently added support for sFlow, see Cisco 8000 Series routers, Cisco ASR 9000 Series Routers, and Cisco NCS 5500 Series Routers.
First, IOS-XR doesn't provide a way to connect to the non-standard BGP port (1179) that sFlow-RT uses by default. Allowing sFlow-RT to open the standard BGP port (179) requires that the service be given additional Linux capabilities.
docker run --rm --net=host --sysctl net.ipv4.ip_unprivileged_port_start=0 \ sflow/ddos-protect -Dbgp.port=179
The above command launches the prebuilt sflow/ddos-protect Docker image. Alternatively, if sFlow-RT has been installed as a deb / rpm package, then the required permissions can be added to the service.
sudo systemctl edit sflow-rt.service
Type the above command to edit the service configuration and add the following lines:
[Service] AmbientCapabilities=CAP_NET_BIND_SERVICE
Next, edit the sFlow-RT configuration file for the DDoS Protect application:
sudo vi /usr/local/sflow-rt/conf.d/ddos-protect.conf
and add the line:
bgp.port=179
Finally, restart sFlow-RT:
sudo systemctl restart sflow-rt
The application is now listening for BGP connections on TCP port 179.
Now configure the router to send sFlow telemetry to sFlow-RT. The following commands configure an IOS-XR based router to sample packets at 1-in-20,000 and stream telemetry to an sFlow analyzer (192.127.0.1) on UDP port 6343.
flow exporter-map SF-EXP-MAP-1 version sflow v5 ! packet-length 1468 transport udp 6343 source GigabitEthernet0/0/0/1 destination 192.127.0.1 dfbit set !
Configure the sFlow analyzer address in an exporter-map.
flow monitor-map SF-MON-MAP record sflow sflow options extended-router extended-gateway if-counters polling-interval 300 input ifindex physical output ifindex physical ! exporter SF-EXP-MAP-1 !
Configure sFlow options in a monitor-map.
sampler-map SF-SAMP-MAP random 1 out-of 20000 !
Define the sampling rate in a sampler-map.
interface GigabitEthernet0/0/0/3 flow datalinkframesection monitor-map SF-MON-MAP sampler SF-SAMP-MAP ingress
Enable sFlow on each interface for complete visibilty into network traffic.
Also configure a BGP Flowspec session with sFlow-RT
router bgp 1
bgp router-id 3.3.3.3
address-family ipv4 unicast
address-family ipv4 flowspec
route-policy AcceptAll in
validation disable
!
!
neighbor 25.2.1.11
remote-as 1
update-source loopback0
address-family ipv4 flowspec
!
!
route-policy AcceptAll
done
end-policy
!
flowspec
local-install interface-all
!
The above configuration establishes the BGP Flowspec session with sFlow-RT.
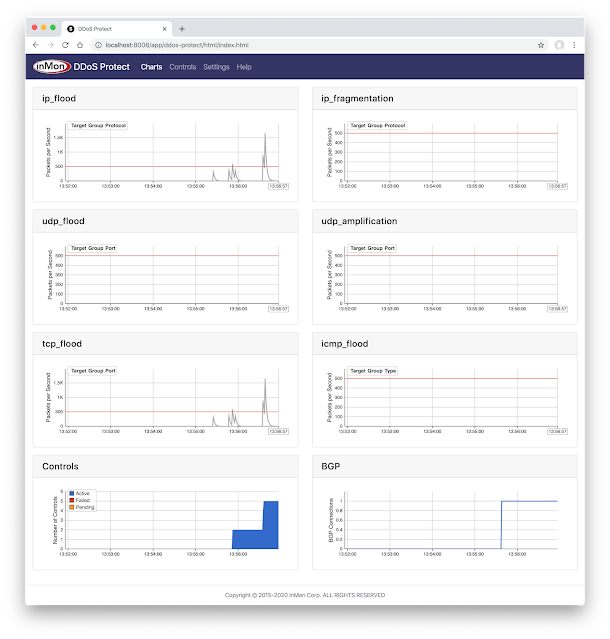
Real-time DDoS mitigation using BGP RTBH and FlowSpec describes how to simulate a DDoS UDP amplification attack in order to test the automated detection and control functionality.
RP/0/RP0/CPU0:ASR9000#**show flowSpec afi-all** Tue Jan 25 08:17:30.791 UTC AFI: IPv4 **Flow :Dest:192.0.2.129/32,DPort:=53/2** Actions :**Traffic-rate: 0 bps** (bgp.1) RP/0/RP0/CPU0:ASR9000#
Command line output from the router shown above verifies that a Flowspec control blocking the amplification attack has been received. The control will remain in place for 60 minutes (the configured timeout), after which it will be automatically withdrawn. If the attack is still in progress it will be immediately detected and the control reapplied.
DDoS Protect can mitigate a wide range of common attacks, including: NTP, DNS, Memcached, SNMP, and SSDP amplification attacks; IP, UDP, ICMP and TCP flood attacks; and IP fragmentation attacks. Mitigation options include: remote triggered black hole (RTBH), filtering, rate limiting, DSCP marking, and redirection. IPv6 is fully supported in detection and mitigation of each of these attack types.

No comments:
Post a Comment